Jump Hosts
Jump hosts are an important part of segmented security architecture. Sandfly is able to use jump hosts to allow it to access isolated segments and perform full security scanning for intruders.
Jump Host View
To add a jump host you first must ensure you have a credential that can work with the jump host to be added. Please refer to the Adding Credentials section on how to do this.
Once the credential is available, go to the Configuration sub-section in the sidebar and select Jump Hosts to go to the Jump Host view.
Jump Hosts in the Sidebar
The Jump Hosts view will display results like shown below. If you have no jump hosts, then the data table will be empty.
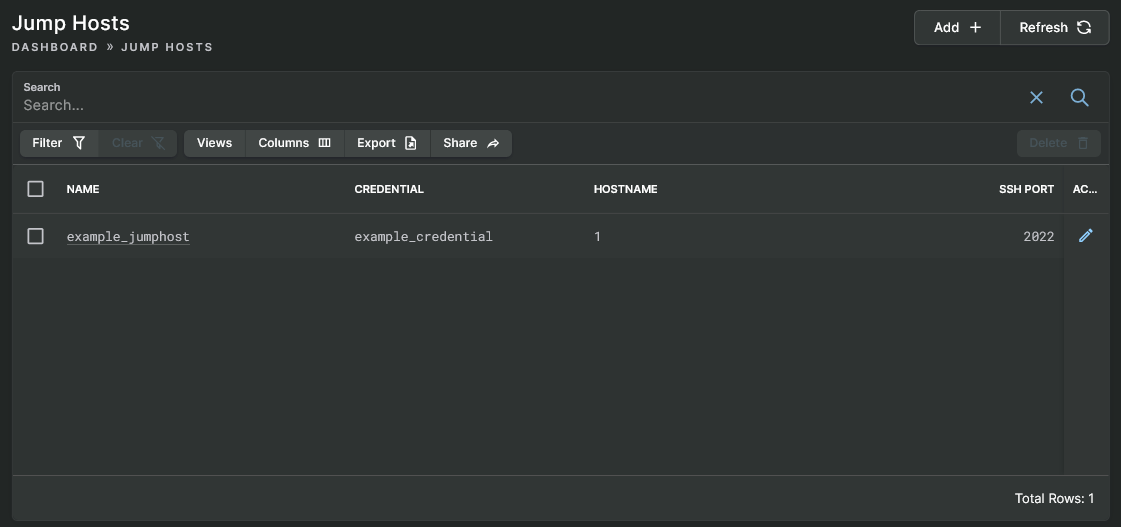
Jump Hosts View
Adding Jump Host
Click on the Add button in the upper right corner of the Jump Hosts view to open the Add Jump Host form, which has a basic set of fields.
Enter into the Name field a snake_case name for the jump host. Then enter into the Hostname field either the hostname or IP address of the jump host. Next, use the Credential drop-down list to select the credential that will work to authenticate to the jump host. Finally, if necessary, change the SSH Port field from the default value to the port that is used by the jump host.
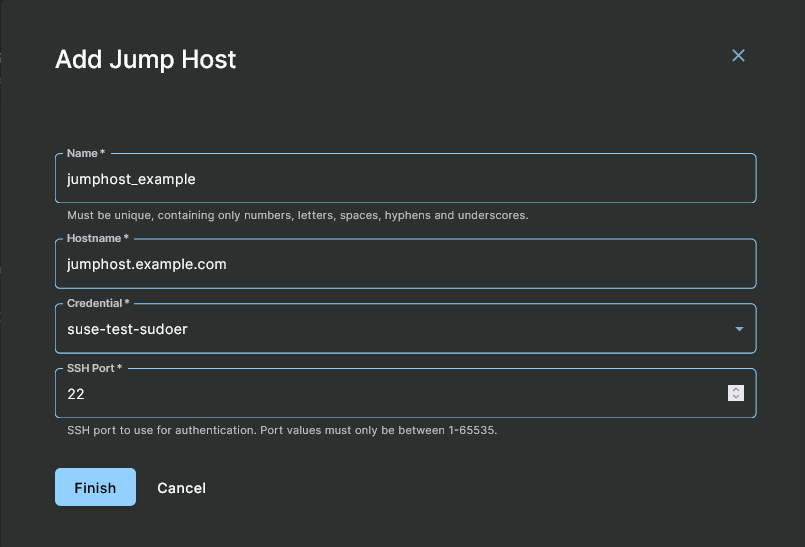
Add Jump Host Form
After you have entered the above information, click on the Finish button and the new jump host will be listed in the Jump Hosts view. You can now use this jump host to add your primary hosts and Sandfly will use the jump host(s) you select to establish the connection.
Use Jump Hosts to Hide Incident Response
Jump hosts can not only be used to help isolate your network, but if you are investigating an incident you may want to setup a chain of hosts to hide your origin. Sandfly will happily use a series of jump hosts to connect to the remote system under investigation. You can easily spin up VMs in the cloud to form a chain of jumps and destroy them when you are done.
This is a valuable tactic for hiding the location of your system from attackers during an incident.
Jump Host MaxStartups in SSH
By default, SSH daemons limit the number of maximum connections that can start at once. This prevents flooding a server with connection attempts. However, Sandfly has many scanning threads and if they all connect to the jump host at once, then many of the connections will be refused.
Noting the above information, you may need to change the MaxStartups option under the system sshd_config to a higher value.
Each Sandfly node container can have up to 500 concurrent scanning threads running at once. If you think you will be operating at this capacity, then you should increase the defaults to something like this:
MaxStartups 500
You will need to restart the SSH daemon of the server for the updated value to take effect.
Updated 3 months ago
