SSH Hunter
Identify, track, and respond to SSH credential use and abuse
SSH Hunter is a powerful tool to track SSH key usage across your Linux systems. SSH Hunter leverages Sandfly's agentless architecture to give you the ability to:
- Track keys across all your systems.
- See which users can access your systems.
- Discover when keys were first and last seen, key types, and key locations.
- Visualize how keys, users, and host access are distributed.
- Find anomalies such as duplicate keys or users with new keys unexpectedly added.
- Rapidly respond to incidents involving compromised SSH credentials.
- Search for new keys, old keys, banned keys, and much more.
This powerful tool gives you the ability to quickly track and identify issues with SSH keys. SSH can be a serious cause of compromise on Linux due to lack of monitoring. SSH Hunter puts you in control of this critical data.
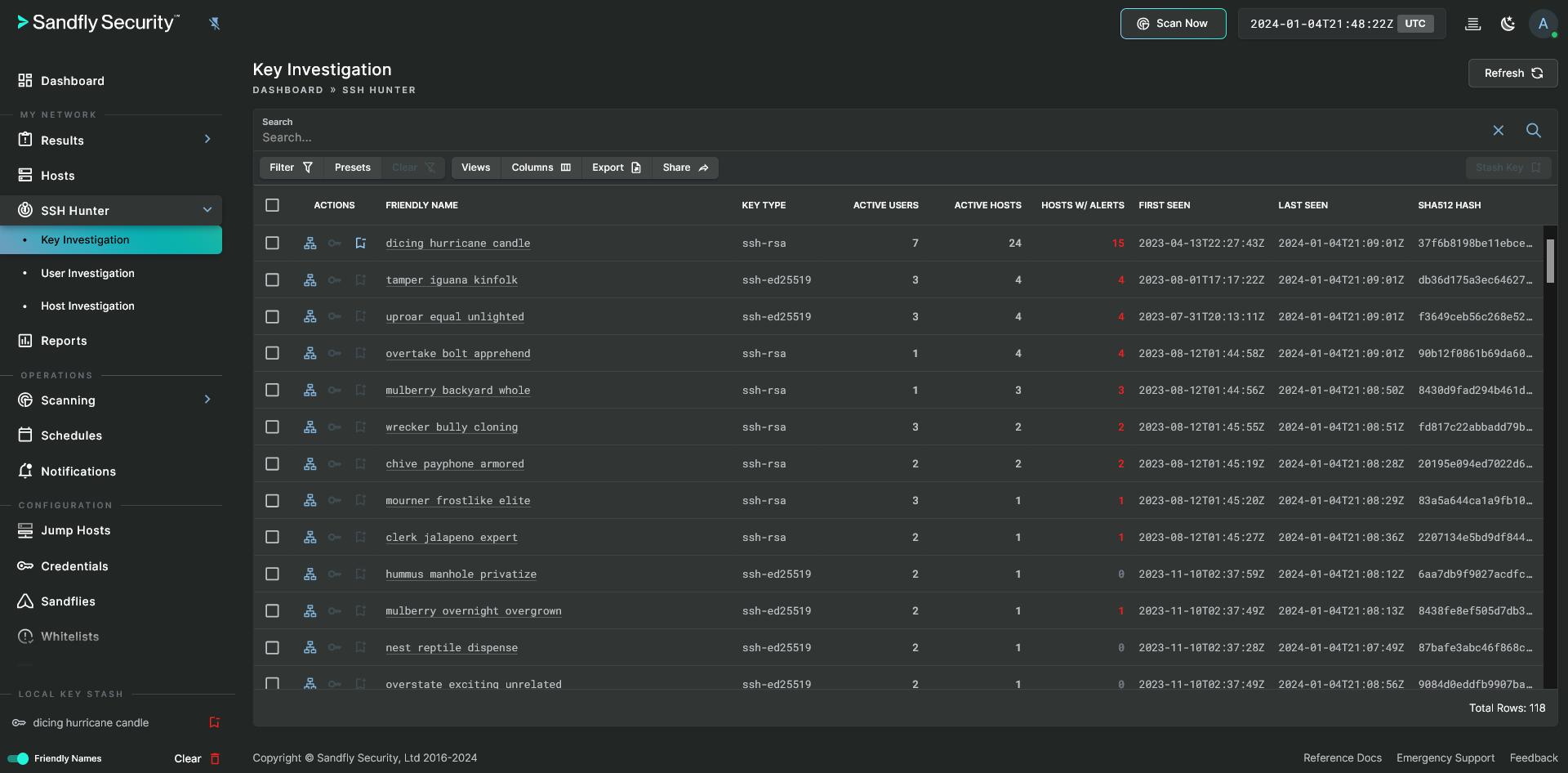
SSH Hunter with Local Key Stash
The SSH Hunter tool consists of the following sub-sections:
- Key Investigation - Provides investigative data that is focused around the use of SSH keys themselves.
- User Investigation - Provides investigative data that is focused around the use of SSH keys by users.
- Hosts Investigation - Provides investigative data that is focused around the use of SSH keys on hosts.
TODO: SSH Hunter needs recon_user_list_all enabled
This tool needs the recon_user_list_all sandfly to be enabled. Without that sandfly, scans will not collect all of the necessary data for full SSH Hunter functionality.
Expanding the SSH Hunter option in the sidebar will display all of the available sub-sections that can be accessed with a click.
Updated 4 months ago
